When discussing the diversity and security of Internet communications, SOCKS5 proxy, as a powerful network transit service, plays a pivotal role. It not only provides anonymity and flexibility in data transmission, but also enhances the security of network communications and the ability to bypass geographical restrictions. This article will explore in depth the working principle of SOCKS5 proxy and its diverse application scenarios, aiming to provide readers with a comprehensive and practical guide.
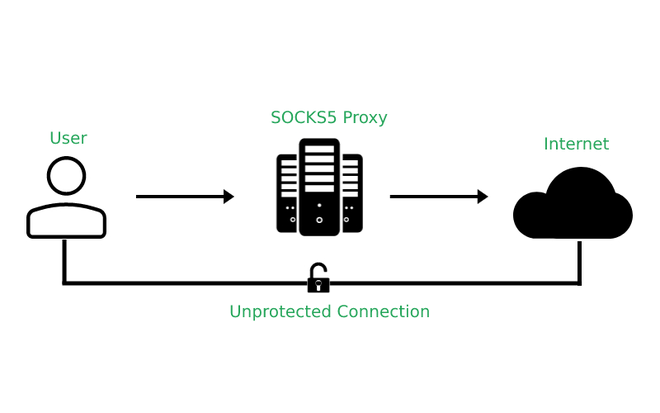
I. How SOCKS5 Proxy Works
1.1 Basic Concepts of SOCKS5 Proxy
SOCKS5 proxy is a network protocol conversion service that sits between the client and the target server and is responsible for forwarding client requests and target server responses. Unlike HTTP proxy, SOCKS5 proxy not only supports HTTP protocol, but also can process TCP and UDP protocol packets, making it applicable to a wider range of network applications, such as email, instant messaging, online games, etc.
1.2 Connection establishment process
The workflow of SOCKS5 proxy starts with the client's request. When the client wants to access a target server through SOCKS5 proxy, it will first send a connection request to the SOCKS5 proxy server. This request contains the address and port number of the target server, as well as the type of protocol (TCP or UDP) that the client wants to use.
After receiving the request, the proxy server will authenticate with the client (if the authentication mechanism is configured). After the authentication is passed, the proxy server will try to establish a connection with the target server. Once the connection is successfully established, the proxy server will forward data between the client and the target server to enable communication between the client and the target server.
1.3 Data transmission
During the data transmission stage, the SOCKS5 proxy server acts as a "transparent" transit station. It does not check or modify the content of the data packet, but simply forwards the data packet from one end to the other. This transparent forwarding mechanism ensures the integrity and anonymity of data transmission.
II. Application scenarios of SOCKS5 proxy
2.1 Privacy protection and anonymous access
One of the major application scenarios of SOCKS5 proxy is privacy protection and anonymous access. Through SOCKS5 proxy, the user's real IP address is hidden and replaced by the IP address of the proxy server. This makes it difficult for attackers to track the user's real identity and location, thereby enhancing the user's privacy protection.
2.2 Bypassing geographical restrictions
Many online services and resources are restricted by geographical location. For example, some video streaming services may only provide services in specific countries or regions. By connecting to a SOCKS5 proxy server located in the target area, users can bypass these geographical restrictions and access restricted resources.
2.3 Network acceleration and optimization
In some cases, SOCKS5 proxy can also be used for network acceleration and optimization. For example, when users access foreign websites or services, the access speed may be affected due to network latency and bandwidth limitations. By connecting to a SOCKS5 proxy server that is located near the user and has a good connection with the target server, users can shorten the network path and increase access speed.
2.4 Security Enhancement
SOCKS5 proxy can also be used in conjunction with encryption technology to further enhance the security of network communications. For example, users can connect to a remote server that supports SSL/TLS encryption through a SOCKS5 proxy to achieve end-to-end encrypted communication. In this way, even if the data is intercepted during transmission, the attacker cannot decrypt and read the data content.
III. Summary
As a powerful network transit service, SOCKS5 proxy has won wide attention and application with its flexibility and security. By deeply understanding the working principle and application scenarios of SOCKS5 proxy, users can better use this tool to protect their privacy, bypass geographical restrictions, optimize network performance, and enhance the security of network communications. Whether for individual users or corporate users, SOCKS5 proxy is a network tool worth considering and using.
Related Recommendations
- What is dynamic IP? What are the advantages of dynamic IP proxies?
- Promote your business with residential agencies
- Want smooth access to ChatGPT? 98IP proxy IP helps you deal with U.S. native IP
- Why is it always dropped when collecting data using dynamic IP? How to solve it?
- How to log in to social accounts in batches: Proxy IP switching steps and considerations
- Tips for selecting dynamic proxy IP pools: The key to successful crawler
- What is the role of IP whitelists?
- Shopify store operations: proxy IP ensures smooth access and data security
- How to prevent overseas social media matrix connections through IP proxies?
- Can two proxy IPs be used on two computers?

